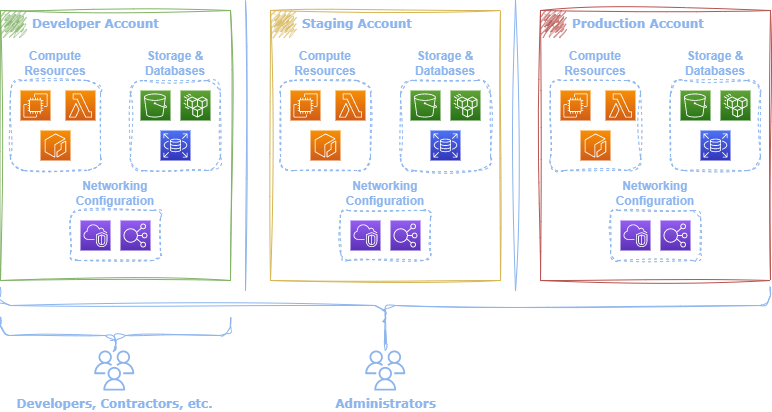
Accounts
After initially signing up for AWS, a default root account is created. AWS accounts function as containers for organizing and isolating cloud resources. For example, deployment environments, such as development, staging, and production, often utilize distinct AWS accounts. In addition, accounts act as a security boundary, ensuring only authorized users and systems can access particular cloud resources. 1
An AWS account has the following unique identifiers:2
- AWS Account ID: 12-digit unique ID
- Canonical User ID: Obfuscated form of the account ID. Used when granting cross-account access to cloud resources.
The active account ID can be fetched from the Security Token Service (STS) with the following CLI command:
Command
aws sts get-caller-identity --query Account --output text
Output
123456789012
The command aws sts get-caller-identity fetches the active user information leveraged by the CLI, which includes the user ID, the account ID, and the user access resource number (ARN). The --query flag enables users to target a particular field to output in the response and --output specifies the desired format (yaml, josn, text, etc.) 3 4
The simplest way to fetch the canonical ID is via the Simple Storage Service (S3) API CLI command.
Command
aws s3api list-buckets --query Owner.ID --output text
Output
79a59df900b949e55d96a1e698fbacedfd6e09d98eacf8f8d5218e7cd47ef2be
-
https://docs.aws.amazon.com/accounts/latest/reference/accounts-welcome.html ↩︎
-
https://docs.aws.amazon.com/general/latest/gr/acct-identifiers.html ↩︎
-
https://docs.aws.amazon.com/cli/latest/userguide/cli-usage-filter.html ↩︎
-
https://docs.aws.amazon.com/cli/latest/userguide/cli-usage-output-format.html ↩︎