Cloud Computing
Exploration of concepts and cloud providers
Exploration of concepts and cloud providers
A brief overview of common cloud computing terms and concepts.
Cloud computing allows developers to provision and manage computational and network resources, such as servers, networks, or data stores, through a web interface, such as a web page or API. The National Institute of Standards and Technology (NIST) formally defines cloud computing as follows:
Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.
Companies and third-parties with cloud computing platform offerings are known as cloud providers. Popular cloud providers incude Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
Cloud computing affords engineers numerous benefits when developing applications, such as:
To enable the on-demand provisioning, cloud providers heavily utilize virtualization to allocate and isolate computational resources and application processes amongst customers. It provides a layer of abstraction of the data center resource pool and can provide interfaces of storage, networking, and computation devices.
While cloud providers often use virtualization, certain use cases prohibit the use of shared CPU/Memory usage due to regulatory requirements. As such, cloud providers typically provide access to physical, non-virtualized hardware at additional costs.
Cloud service offerings typically provide trade-offs between user configurability, costs, and overhead, ranging from fully user-configurable servers and virtual environments to completely managed services, such as for databases. Cloud services are broadly categorized as:
The rise of cloud computing has accelerated the adoption of practices for developing robust cloud applications, collectively known as cloud-native development. These practices include microservices, containerization, and serverless development for improving application scalability, portability, deployability, and development speed.
An increasing number of companies are either leveraging cloud computing or considering migrating existing on-premise applications to the cloud. Because of this, it is important for developers to be aware of the common benefits of working in such environments.
In traditional on-premise environments, if software engineers required additional infrastructure for hosting or scaling web services, a considerable amount of time was necessary to install and configure the hardware within an organization’s private data center. Conversely, cloud resources can typically be provisioned anywhere between a few seconds to a few minutes through a web API call. This on-demand provisioning of resources enables more rapid development and experimentation
Cloud computing can potentially be more economical than traditional on-premise hosting. Cloud resources can be provisioned with no up-front cost, instead utilizing a pay-as-you-go model. All hardware management is offloaded from organizations to the cloud provider. Additionally, because cloud providers purchase hardware in bulk, they are able to leverage economies of scale and pass those savings onto cloud customers.
Readers should note that the above is a broad generality and should always consider the specifics of their organization when performing a cost-benefit analysis. For instance, Dropbox initially developed their SaaS platform using cloud technologies, notably AWS S3, before later migrating to their own infrastructure, which increased product performance and cost-effectiveness.
Cloud providers have more computational resources available than most private data centers. Therefore, cloud services can be more readily scaled to account for increases or decreases in application load. A common example would be online retailers provisioning more servers for handling holiday traffic. Conversely, resources can be scaled down to save on costs, such as outside business hours.
There are two types of scaling, horizontal and vertical. Horizontal scaling refers to the addition or removal of servers to account for increased load in a distributed fashion. This type of scaling typically can be accomplished with minimal delay or application downtime.
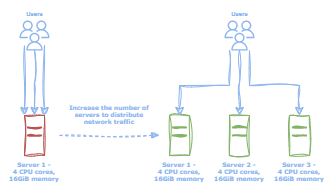
Figure 1: With horizontal scaling, additional resources may be provisioned to handle increases in system load.
Vertical scaling refers to modifying the underlying hardware configuration of cloud resources, such as memory, CPU, or storage. This operation is typically disruptive and may result in application downtime.
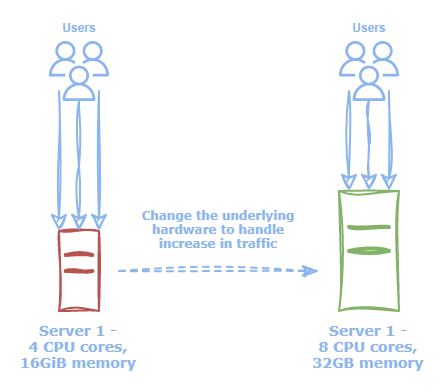
Figure 2: Vertical scaling changes the underlying hardware configuration for cloud resources, such as CPU or memory.
For on-premise applications, companies manage all the underlying compute, storage, and networking infrastructure for their systems and services. Cloud computing can manage some or all of these aspects for their customers, depending on the type of service classification. There are three cloud computing service models, Infrastructure as a Service (IaaS) Platform as a Service (PaaS), and Software as a Service (SaaS). 1 2
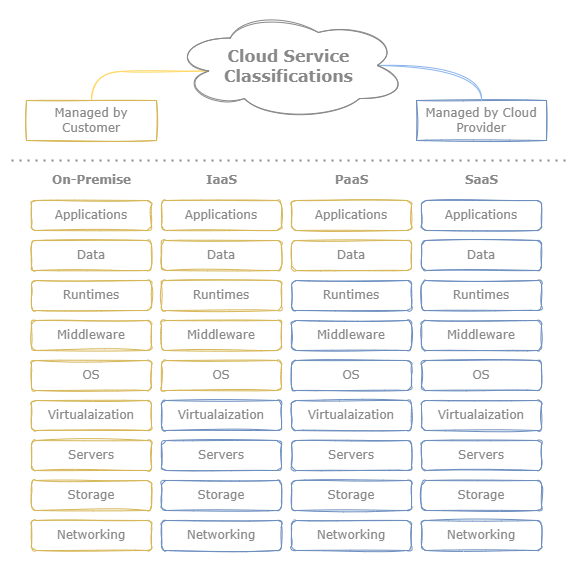
Figure 1: Cloud computing service classifications.
IaaS provides virtualized or physical servers for hosting applications. Cloud providers maintain the underlying network and hardware infrastructure while allowing cloud engineers control of the host OS and software. The hardware can be configured upon initially provisioning a new service, such as CPU, memory, storage, networking, GPU, etc. AWS EC2 service provides virtual servers known as instances for developers to host applications.
PaaS manages all the components maintained by IaaS services in addition to host operating system and execution runtime, allowing users to primarily focus on application development. PaaS offerings typically manage infrastructure autoscaling, monitoring, and logging. Examples of PaaS would be Heroku, which allows developers to upload their applications to a server without having to worry about provisioning the underlying hardware or OS. The AWS offers a similar service known as Elastic Beanstalk.
A related offering would be Functions as a Service (FaaS), which, similar to PaaS services, allows for developers to deploy and execture code in the cloud. However, unlike PaaS, FaaS services tend to run in more restricted environments, such as limited CPU and memory configuration, execution time, application size, etc. while running in a more ephemeral environment.
For SaaS services, users manage none of the underlying infrastructure or application logic and are instead strictly service consumers. An example of this would be Dropbox or the AWS S3 service, where users can upload data through a web console or API while AWS maintains all backend storage.
NIST Definition of Cloud Computing: https://csrc.nist.gov/publications/detail/sp/800-145/final ↩︎
AWS Types of Cloud Computing: https://aws.amazon.com/types-of-cloud-computing/ ↩︎