Introduction
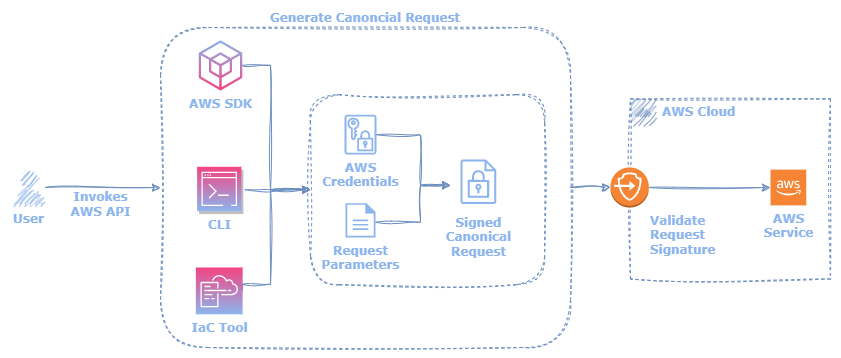
AWS cloud services are available through public API endpoints. Whether invoked via the AWS CLI, SDKs, or Infrastructure as Code (IaC) tools, each approach ultimately results in sending HTTP requests to AWS service endpoints. These underlying HTTP requests are referred to as canonical requests.
AWS canonical requests include a signature generated with request parameters and AWS secret key. This signature enables AWS to validate the identity of the client, protect the API request data in transit, and mitigate potential relay attacks.
While developers may directly create, sign, and transmit canonical requests to AWS, it is often preferable to utilize the AWS-provided CLI and SDKs. Direct canonical calls to AWS are primarily recommended in cases when developing in unsupported programming languages or where fine-grained API control is required.
Request Structure
Canonical requests are composed of the following component:1
CanonicalRequest =
HTTPRequestMethod + '\n' +
CanonicalURI + '\n' +
CanonicalQueryString + '\n' +
CanonicalHeaders + '\n' +
SignedHeaders + '\n' +
HexEncode(Hash(RequestPayload))
The individual components are defined below:
- HTTPRequestMethod: The HTTP operation
- CanonicalURI: Absolute path of the target resource, including the base service domain.
- CanonicalQueryString: URI-encoded query parameters
- CanonicalHeaders: List of all the HTTP headers included with the signed requests.
- SignedHeaders: Alphabetically sorted, semicolon-separated list of lowercase request header names
- RequestPayload: Payload of the target request. This is hashed and hex encoded for additional security.